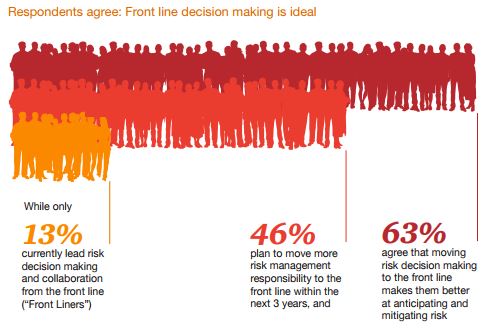
Despite recent volatility, more than 60% of risk executives surveyed in a recent PwC US Pulse Survey were optimistic about the global economy, as well as the state of the pandemic recovery. This optimism could stem from a greater alignment between risk functions and the business. Fifty percent of risk management executives reported interacting more with the C-suite, and 42% said they interact more with the board level. Nearly half of respondents said that risk functions and capabilities are now embedded in the business operations that are driving transformations.
Risk functions were once considered tactical and reactive, and often seen as a roadblock to business decisions. Infusing risk management into corporate planning allows an organization to think about compliance responsibilities in a proactive and strategic manner—moving risk and regulatory functions from a back-office cost to a competitive advantage. Staying ahead of uncertainties while also bolstering planning with data helps make companies stronger and more resilient.
Many companies spent the last decade overspending on risk management as they attempted to keep up with compliance and regulatory shifts, frequently lagging behind changes in policy. They often invested heavily in new technologies and data collection, but failed to create efficiencies by integrating those systems across largely siloed business functions. The swift onset of the pandemic made many organizations come to terms with the reality that an entire organization didn’t need to be reimagined in order to implement technological transformations, and that there was still a disconnect between many of the piecemeal systems that had been previously put in place.
Now, executives are increasingly seeing the value of risk management as a strategic advantage. It allows companies to grow in areas with less mature risk management functions, like taking on higher risk clients or entering new geographies. More intelligent monitoring also allows for increased efficiencies and reduced compliance costs.
Integrating AI and automation into the investments that have already been made can help streamline the risk management and compliance processes. Many companies still have room for improvement; only 25% of risk professionals said they were implementing new risk management technologies in 2021 and only 19% said it was a priority to integrate risk management tools onto a single platform.
By automating and enhancing risk management functions, organizations can:
- Strategize for entering new markets. Make more informed decisions about entering a new market by taking into consideration a shifting regulatory environment and increasingly complex supply chains. Taking on high risk customers relies on analytics and transaction monitoring systems in order to identify potential suspicious activity.
- Increase speed to respond. Automation and technology-led monitoring of policy and negative news helps position companies to respond more quickly to regulatory bodies and head off negative events before they go viral.
- Allocate costs efficiently. No longer duplicate costs by operating the departments of your business in a siloed fashion. Leverage case management and workflow systems to aggregate control failures or suspicious activity by customer or focal entity, allowing you to evaluate the root cause and apply analysis across multiple control failures.
- Enter new business partnerships more confidently. Know the risks of a potential business partnership and get deeper insights into the impact a business partner or vendor’s supply chain could have on your business. Vendor risk management and contract analytics technologies can monitor whether business partners are adhering to their terms and conditions.
- Reduce the impact of new requirements. Identify the blind spots and shed light on the potential risks within your enterprise system so you can quickly take action early in the process, allowing your organization to avoid fines when implementing new regulatory requirements.
Regulators and other stakeholders are increasingly calling for the organization of risk management functions under one cohesive point of view. By fixing the disconnects and setting a collaborative tone, you give senior executives more cohesive insights and allow them to adopt more extensive views on the organization’s risk profile.