NEW YORK—At yesterday’s Advisen Cyber Insights Conference, Zurich and Advisen released the fifth annual Advisen Cyber Survey of U.S. risk managers, finding a 9% acceleration in cyber liability insurance purchasing from 2014 to 2015. The firm has seen a 26% increase in the number of respondents who have coverage since the first survey in 2011.
Companies are taking cyberliability more seriously, Zurich reports, with the number of organizations developing data breach response plans up 10% from last year. What’s more, companies appear to be better recognizing the sheer amount of value at risk, with two-thirds of respondents saying they have either increased their policy limits or are considering doing so. While Zurich found that more organizations view information security as an organizational challenge rather than the purview of the IT department alone, and respondents said that boards and executive management are taking cyberrisk more seriously, those who have not yet obtained cyber coverage say it is because their superiors still do not see the need. There is also still a considerable difference in take-up rates among large corporations and small and mid-sized businesses, with Catherine Mulligan, senior vice president and national underwriting manager of specialty E&O, telling the audience there is an approximate 20-point spread between the groups.
“This year’s cyber survey shows that demand for coverage and higher limits has increased tremendously and we at Zurich have seen double digit growth year over year,” said Bryan Salvatore, president of specialty products for Zurich North America. “That is why we are heavily invested in identifying risks and delivering solutions and why we are committed to staying at the forefront of this issue.”
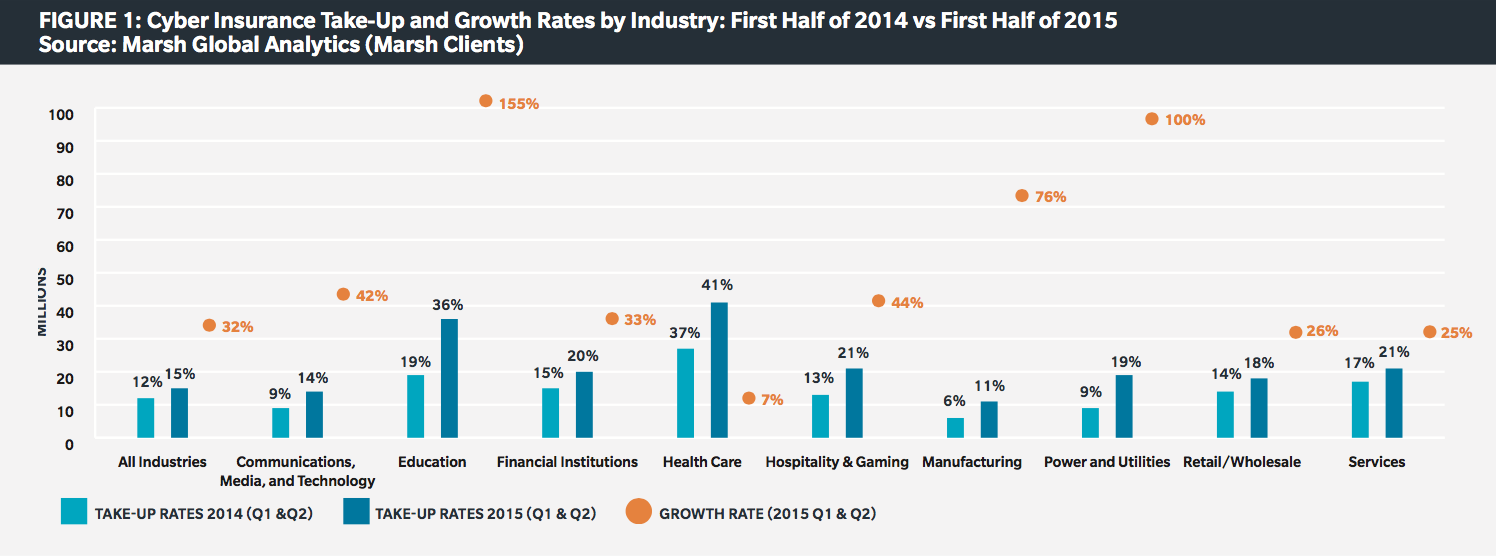
Marsh has also seen considerable growth in cyber liability insurance purchasing among its clients. According to the insurer’s new midyear cyber benchmarking report, the number of U.S.-based Marsh clients purchasing standalone cyber insurance increased 32% in the first half of 2015, up from 26% growth during this period in 2014. By sector, members of the education industry made up the biggest growth, with 155% more clients purchasing the coverage, followed by power and utilities with a 100% increase and manufacturing with a 76% increase. The healthcare sector remains Marsh’s largest buyer of cyber coverage, with 41% of all clients in this industry purchasing it by the end of the first half of 2015.
Sessions throughout the conference made clear that insurers—and the industry at large—are still struggling with what is also risk managers’ biggest challenge: data. Completely evaluating the true value at risk with cyber liability continues to elude both sides, although many new approaches and consultancy services are emerging. Further, the dearth of actuarial data not only compounds the challenges of the cyberrisk assessment process, but make it hard for the industry to set pricing and limits with confidence.
“It is hard for insurers to be prudent with cyber as risk managers often do not fully understand how to measure their exposure,” Mulligan said.
“Actuarial data is the Holy Grail of the cyberinsurance market: we’re all searching for it and it’s just not there,” said Bob Parisi, cyber product leader at Marsh, who moderated a session on the struggle to quantify and model cyberrisk.
In addition to the actuarial uncertainty, the considerable number of large losses over the past few years is continuing to push up the cost of cyber, forming what Willis executive vice president Peter Foster described as a “hot” market that will have to cool and solidify with time. Parisi chose to describe the market as “brittle” after absorbing several hundred million dollars in losses, and a range of insurers and brokers reported that premiums have increased dramatically as a result. The Marsh study found that price increases across industries averaged 19%, with 32% increases among retailers, the most frequently breached sector over the past few years.
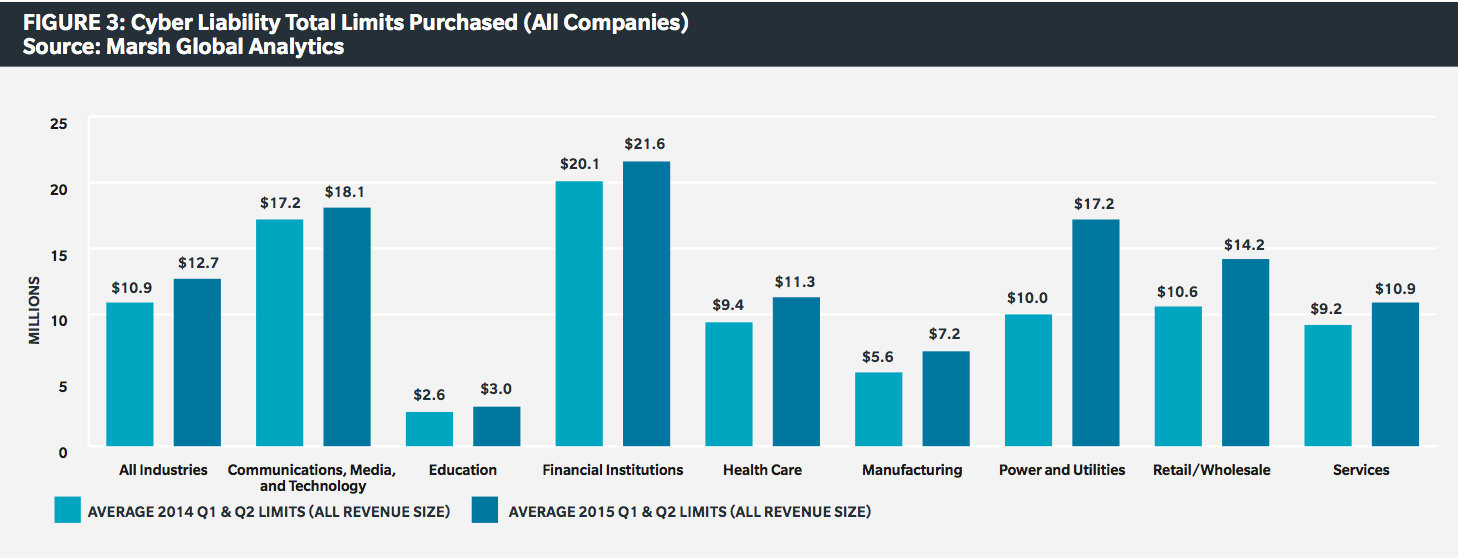
While these breaches and better estimates of the real cost of cyber incidents have helped many companies realize they may be underinsuring for cyber liability, the move to correct this is getting more difficult. Insurers have said repeatedly that there is plenty of capacity in the cyberinsurance market and many buyers have increased the limits purchased, but higher limits of liability are increasingly hard to come by, and none really exist in excess of $100 million. Particularly for businesses that have yet to implement serious efforts to address information security, rate increases appear sure to continue, and simply buying more coverage will not only be unsustainable, but may not even be possible as insurers give more thought to the capacity they are willing to commit to these risks.
“There is just not enough capacity to extend $50 to $100 million limits to every account,” said Greg Vernaci, AIG’s head of cyber in the United States and Canada. “We are looking to reward those companies with a robust information security posture who go beyond and take a multifaceted approach to managing cyberrisk.”




