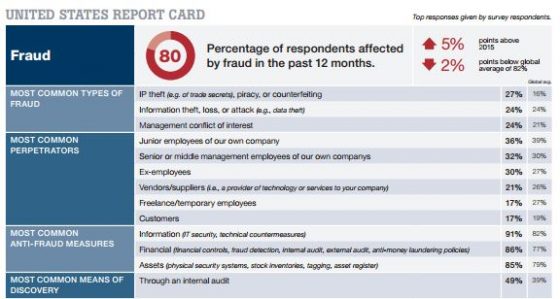
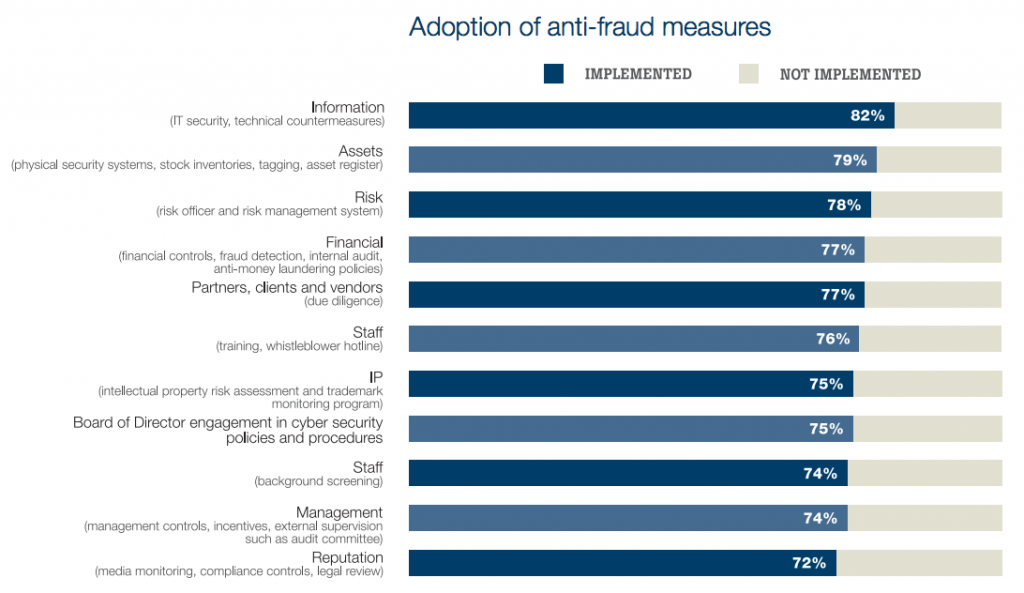
Claimant fraud and premium fraud are two of the most well-known types of workers compensation fraud. In these cases, a worker may intentionally fake an injury (claimant fraud) or a business owner may misrepresent their employee headcount or incorrectly classify employees to obtain lower insurance premiums. Now, a lesser-known type is occurring with greater frequency: provider fraud.
Provider fraud occurs when a professional other than the injured worker or employer accepts a bribe or illegal kick-back in exchange for patient or client referrals. The circle of potential culprits includes lawyers, translators, doctors, chiropractors, nurses, and telehealth professionals. Opportunity, incentive and rationalization—the “fraud triangle”—are key factors that go into a person’s decision to commit insurance fraud. These factors have been exacerbated in recent years, due in large part to the pressures presented by the global pandemic and the growing reliance upon remote services.
Most schemes involve knowingly billing for medical goods and medical and legal services that are unnecessary or not provided at all. A chiropractor, for example, conducted illegal medical evaluations and billed these evaluations, claiming that he was approved as a medical legal evaluator. In another example, an attorney named his daughter as the owner of a translation services company, while in reality he maintained ownership of the business. Each time the attorney was hired, the translation business was also engaged and billed its services. Provider fraud is increasingly prevalent in California and Florida due to each state’s workers comp rules. For instance, in California, a provider can file their own lien with the Workers’ Compensation Appeals Board, even if the bill was denied. California is the only state that allows providers to file their own adjudication. At a higher rate than in other states, healthcare providers in California and Florida are sometimes found billing for services that were never rendered, billing for more expensive services than were actually provided, ordering unnecessary tests or procedures, and providing kickbacks to referring physicians.
So, how can we pin down provider fraud?
- Review Provider Invoices and Reports: Risk professionals can spot potential fraud cases and fraud trends by closely reviewing provider invoices and reports and scrutinizing those invoices that are close to, but not at the top of, typical billing charges. In the workers compensation system, there are typically five levels of a doctor evaluation: Level 1 is the cheapest while Level 5 is the most expensive. Fraud often occurs in Level 4 billings since Level 5 would be too obvious. Providers who consistently bill at Level 4 could be a red flag for fraud.
- Shine a Spotlight on Supplementary Services: Insurers sometimes overlook that provider fraud can occur with supplementary services such as translation and transportation companies, copy services, medical equipment suppliers and pharmacies. It is not uncommon for insurers to discover that these schemes may involve a criminal enterprise (possibly a referral network) orchestrated by individuals who are not medical or legal professionals. While claimants can be complicit, often they are unwittingly involved and potentially subject to treatment that is unnecessary or even harmful.
- Consider Emerging Tech to Pinpoint Provider Fraud: Artificial intelligence and machine learning are game-changers for fraud investigations. Through the analysis of historical claims data and insurance adjuster notes, some technologies can help professionals discover fraudulent claims faster. For instance, AI can be particularly effective at the entity level when a doctor or hospital that is identified as fraudulent can be added to a “bad actors” list for review in future claims. If you do not have a fraud feedback loop, start gathering information now. As risk and insurance professionals, we rely on business rules and claims adjusters to catch all the details of a claim and then form a cohesive narrative to investigate. While business rules work, the fraud feedback loop is necessary to effectively train machine learning models to detect patterns and flag anomalies.
Workers compensation insurance provider fraud has become a multi-billion-dollar industry that is bad for business. It is costly for insurance companies to identify and prosecute, it inflates costs for goods and services that honest business owners rely on, and it stokes consumer apathy and distrust in the insurance system. Risk and insurance professionals need to be aware of the warning signs so they can work diligently to detect and prevent it.