As companies continue to navigate the changing work environment brought on by the pandemic, it has become clear that business leaders will need to get comfortable revising and adapting their strategies to deal with disruption brought on from new technologies and new regulation. As risk management professionals, these rapid changes have made our job more important than ever to our organizations.
Yet the majority of our organizations—particularly in C-suites—remain far from giving risk management experts the seat at the table they need to effectively safeguard against enterprise threats, digital or otherwise.
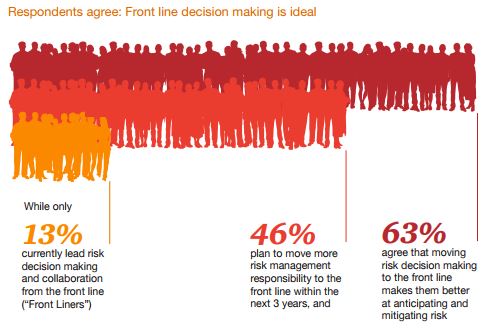
Data from PwC’s Global Risk Survey 2022 shows that executives are starting to recognize these risks: 79% of executives report that they view the breakneck speed of digital transformation as a significant risk management challenge. Moreover, this renewed focus is translating into increased funding, as 65% of organizations are increasing their spending on risk management technology and 56% said they planned to invest in risk culture and behavioral risk in 2022.
Unfortunately, the survey also found that too many organizations are treating the risk function as an add-on or incorporating risk leaders into strategic conversations too late. Only 39% of business leaders reported adding risk professionals to decision-making processes early, which should be an essential step for executives seeking to minimize risk from the outset. On a broader scale, executives seemed to lack confidence in risk managers, with only 47% of respondents saying they feel “very confident” in their risk function’s ability to build a more risk-aware culture, a key element of any successful risk-focused company.
Particularly as companies invest in emerging technologies, business leaders need to listen more to their risk and compliance functions and integrate them into conversations about how those technologies will be implemented. Artificial intelligence is a great example: when companies rush to implement systems to accelerate efficiency and analyze trends, they risk creating disproportionate bias and violating personal privacy through data sourcing. Risk professionals need to be at the table from beginning to end to make sure that an evolving regulatory environment and other pitfalls are fully accounted for in the organization’s implementation process.
While investment in risk management technology is helpful, it is insufficient without making structural changes to the organization to prioritize the risk function company-wide. Particularly as companies consider adopting emerging technologies, the following steps should be considered not just by risk management professionals, but across the C-suite:
- Identify, categorize, and prioritize technology risks across the company. This should be done on a regular basis by a dedicated risk management team, married with the best tools available, with findings routinely reported back to senior leaders. Companies are on the right track here: 65% plan to increase their technology spend this year across data analytics and process automation to support detection and monitoring of risks. This initial step will lay the framework for the establishment of cyber threat intelligence, systems monitoring, and incident response protocols.
- Adapt IT governance to the emerging technologies being adopted. Risk professionals should work with IT teams and company leadership to create governance structures that integrate seamlessly with corporate strategy, allowing for alignment of day-to-day operations, effective decision-making, a framework for best practices, and promotion of investments that enhance business objectives.
- Update leadership often on the emerging tech regulatory landscape. Whether across data privacy rules, cyber reporting requirements, or other complex technology challenges, a robust compliance program should keep leaders across the company updated as new technologies are implemented. Otherwise, companies risk run-ins with legal authorities and the erosion of trust from their clients and customers.online pharmacy cymbalta with best prices today in the USA
- Set expectations with leadership that not all risks are one and the same. Understanding the context around each piece of technology will become imperative to understanding its specific risks and the appropriate response strategy, including the maturity and complexity of the business processes to determine true risk to the company. Inherent in this case-by-case evaluation is an understanding of the company’s risk appetite and criteria for acceptable level of risk.
When adopted purposefully, emerging technologies can make companies more efficient, more profitable, and better stewards for their employees, clients and communities. Risk is often unavoidable for early adopters of emerging technologies, but it can be mitigated if C-suites equip their risk functions with a holistic strategy and a voice in key business decisions. As C-suites and organizations seek to adapt to a changing world, their success will hinge on the extent to which risk management is incorporated into their strategies.

 A quick look at recent headlines shows how quickly a cybersecurity incident can damage a corporate brand. Many companies that have recently experienced data breaches also have been exposed by the media because of ineffective or nonexistent integrated risk management strategies. This can be for a variety of reasons, from executives trying to hide the breach to the belief that they can resolve the issue before it grows into something larger or, possibly the worst of the options, they are not aware that the breach is even occurring.
A quick look at recent headlines shows how quickly a cybersecurity incident can damage a corporate brand. Many companies that have recently experienced data breaches also have been exposed by the media because of ineffective or nonexistent integrated risk management strategies. This can be for a variety of reasons, from executives trying to hide the breach to the belief that they can resolve the issue before it grows into something larger or, possibly the worst of the options, they are not aware that the breach is even occurring.