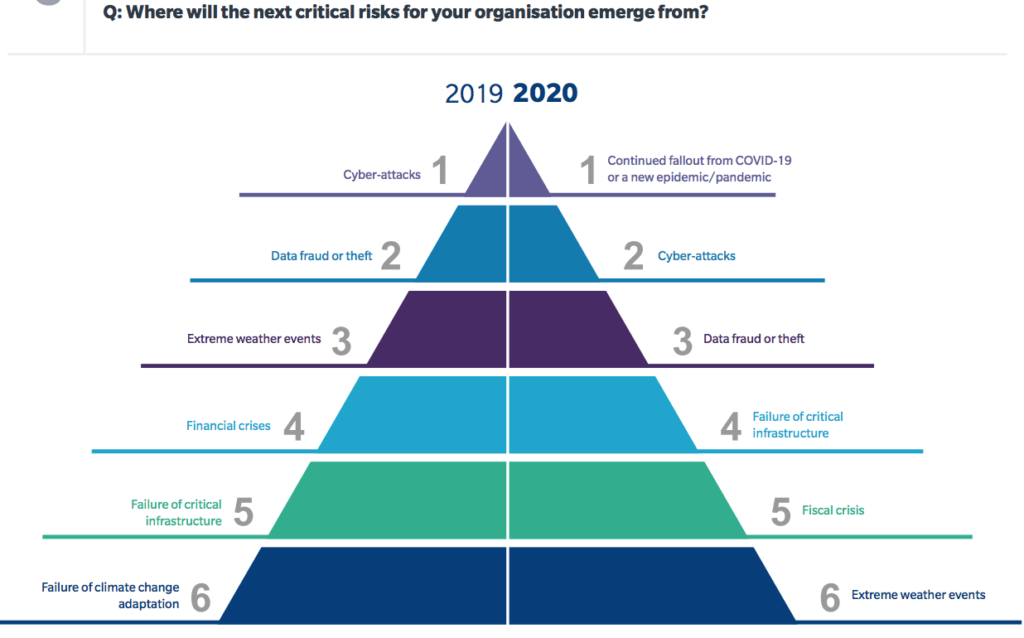
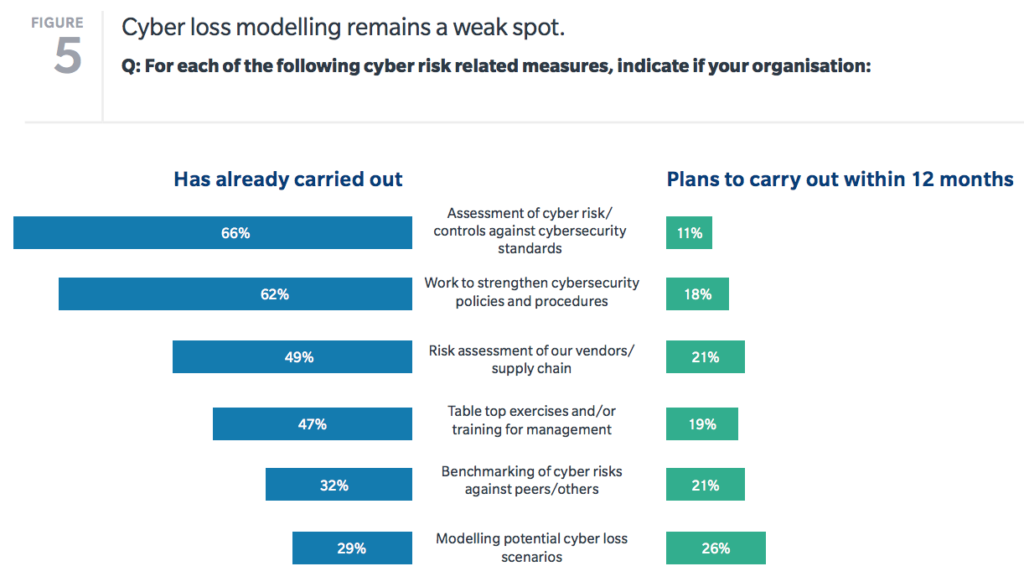
Happy Data Privacy Day! Whether it is cyberrisk, regulatory risk or reputation risk, data privacy is increasingly intertwined with some of the most critical challenges risk professionals face every day, and ensuring security and compliance of data assets is a make or break for businesses.
In Cisco’s new 2021 Data Privacy Benchmark Report, 74% of the 4,400 security professionals surveyed saw a direct correlation between privacy investments and the ability to mitigate security losses. The current climate is also casting more of a spotlight on privacy work, with 60% of organizations reporting they were not prepared for the privacy and security requirements to manage risks with the shift to remote work and 93% turning to privacy teams to help navigate these pandemic-related challenges. Amid COVID-19 response, headline-making data breaches and worldwide regulatory activity, data privacy is also a critical competency area for risk professionals in executive leadership and board roles, with 90% of organizations now asking for reporting on privacy metrics to their C-suites and boards.
“Privacy has come of age—recognized as a fundamental human right and rising to a mission-critical priority for executive management,” according to Harvey Jang, vice president and chief privacy officer at Cisco. “And with the accelerated move to work from anywhere, privacy has taken on greater importance in driving digitization, corporate resiliency, agility, and innovation.”
In honor of Data Privacy Day, check out some of Risk Management’s recent coverage of data privacy and data security:
CPRA and the Evolution of Data Compliance Risks
Also known as Proposition 24, the new California Privacy Rights Act (CPRA) aims to enhance consumer privacy protections by clarifying and building on the expectations and obligations of the California Consumer Privacy Act (CCPA).
Frameworks for Data Privacy Compliance
As new privacy regulations are introduced, organizations that conduct business and have employees in different states and countries are subject to an increasing number of privacy laws, making the task of maintaining compliance more complex. While these laws require organizations to administer reasonable security implementations, they do not outline what specific actions should be taken. Proven security frameworks like Center for Internet Security (CIS) Top 20, HITRUST CSF, and the National Institute of Standards and Technology (NIST) Framework can provide guidance.
Protecting Privacy by Minimizing Data
New obligations under data privacy regulation in the United States and Europe require organizations not only to rein in data collection practices, but also to reduce the data already held. Furthering this imperative, over-retention of records or other information can lead to increased fines in the case of a data breach.
As a result, organizations are moving away from the practice of collecting all the data they can toward a model of “if you can’t protect it, don’t collect it.”
3 Tips for Protecting Remote Employees’ Data
As COVID-19 continues to force many employees to work from home, companies must take precautions to protect sensitive data from new cyberattack vulnerabilities. That means establishing organization-wide data-security policies that take remote workers into account and inform them of the risks and how to avoid them. These three tips can help keep your organization’s data safe during the work-from-home era.
What to Do After the EU-US Privacy Shield Ruling
It was previously thought that the EU-US Privacy Shield aligned with the EU’s General Data Protection Regulation (GDPR), but following the CJEU’s recent ruling, the Privacy Shield no longer provides a mechanism for legitimizing cross-border data flows to the United States. This has far-reaching consequences for all organizations that currently rely on it. In light of the new ruling, risk professionals must help their organizations to reevaluate data strategies and manage heightened regulatory risk going forward.
The Risks of School Surveillance Technology
Schools confront many challenges related to students’ safety, from illnesses, bullying and self-harm to mass shootings. To address these concerns, they are increasingly turning to a variety of technological options to track students and their activities. But while these tools may offer innovative ways to protect students, their inherent risks may outweigh the potential benefits. Tools like social media monitoring and facial recognition are creating new liabilities for schools.
As regulations like CCPA and GDPR establish individuals’ rights to transparency and choice in the collection and use of their personal data, one can expect to see more people exercise these rights.
In turn, businesses need to ensure they have formal and efficient processes in place to comply with such requests in the clear terms and prompt manner these regulations require, or risk fines and reputation fallout. These processes will also need to provide sufficient documentation to attest to compliance, so if businesses have not yet already, they should be building auditable and iterative procedures for “data revocation.”
Data Privacy Governance in the Age of GDPR
As personal information has become a monetizable asset, risk, compliance and data experts have increasingly been forced to address the regulatory and operational ramifications of the rapid, mass availability of personal customer and employee data circulated both inside and outside of organizations. With new data protection regulations, Canadian and U.S. companies must reassess how they process and safeguard personal information.
Key Features of India’s New Data Protection Law
Among the new data protection laws on the horizon is India’s Personal Data Protection Bill. While the legislation has not yet been approved and is likely to undergo changes before it is enacted, its fundamental structure and broad compliance obligations are expected to remain the same. Companies both inside and outside India should familiarize themselves with its requirements and begin preparing for how it will impact their data processing activities.