 High-profile data breaches have been making headlines recently, and their damage can transcend industries, which is why cybersecurity is often a top priority for risk managers. With many traditional insurance policies no longer responding to or outright excluding cyber events, risk professionals must understand their options to ensure the organization is protected in the event of a data breach.
High-profile data breaches have been making headlines recently, and their damage can transcend industries, which is why cybersecurity is often a top priority for risk managers. With many traditional insurance policies no longer responding to or outright excluding cyber events, risk professionals must understand their options to ensure the organization is protected in the event of a data breach.
A new report by RIMS, A Guide to Cyber Insurance, provides a roadmap for determining the type of coverage risk managers need in the fast-changing world of privacy, data protection, and cyber risk management. The study serves as a reference for risk professionals who are exploring options to effectively manage cyberrisks that are uncovered or not addressed by the organization’s existing risk management program.
Topics include:
- The cyber insurance application process
- Procurement of insurance
- Management of cyber claims
- Third-party coverage
- Litigation strategies, and other pertinent details
“While cyber risk management policies are necessary for every organization, reducing a category of risk to zero is impossible,” the report notes. “Cyber insurance can help cover the gaps between a robust risk management program and any remaining risks.”
The report also features case reviews in the areas of cyber policy coverage litigation, negligence, computer fraud, technology errors and advertising and personal injury coverage. “While the overall decision-making process is much the same as with other litigation decisions, certain factors are more complex in the cyber insurance context compared to other insurance disputes,” the authors note.
The Guide doesn’t only focus on insurance. It also features helpful tips when implementing a strategic risk management program characterized by a cybersecurity framework. Pre-event planning and preparation, penetration testing and response ideas are offered as well.
“Following the purchase of some form of cyber coverage, risk professionals need to be prepared for the worst: a cyber event and any resulting claims,” the report states.
“An organization needs to understand both the risk it faces and the coverage options available to ensure that the cyber policies it purchases provide the necessary coverage when it experiences the inevitable data breach or other cyber events.”
A Guide to Cyber Insurance is authored by Bradley Arant Boult Cummings law firm members: Dylan C. Black, A. Kate Margolis, G. Benjamin Milam and Emily M. Ruzic.
The report is currently available to RIMS members.
To download the report, visit the RIMS Risk Knowledge library at www.RIMS.org/RiskKnowledge. To learn about other RIMS publications, educational opportunities, conferences and resources, visit www.RIMS.org.

 urity industry, noting that, “the defense trails the offense by about five years.” Comparing the newest waves of protection software to a strong rookie pitcher, he said, “A new pitcher may come along and strike everybody out as he goes through the league a few times. But eventually he gets figured out and [hackers] figure it out,” he said. “It needs at least a year of being attacked for real,” to find the gaps in efficiency, and leads to the “the kind of experimentation that will yield better results.”
urity industry, noting that, “the defense trails the offense by about five years.” Comparing the newest waves of protection software to a strong rookie pitcher, he said, “A new pitcher may come along and strike everybody out as he goes through the league a few times. But eventually he gets figured out and [hackers] figure it out,” he said. “It needs at least a year of being attacked for real,” to find the gaps in efficiency, and leads to the “the kind of experimentation that will yield better results.”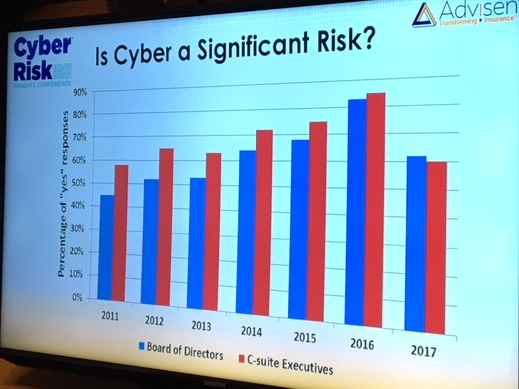 Advisen
Advisen 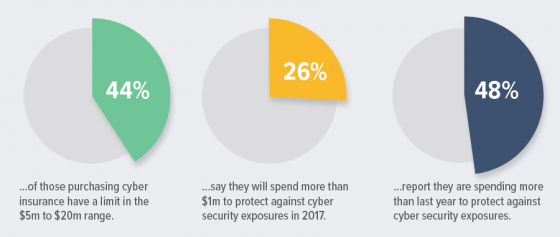 Key findings from this year’s RIMS Cyber Survey include:
Key findings from this year’s RIMS Cyber Survey include: