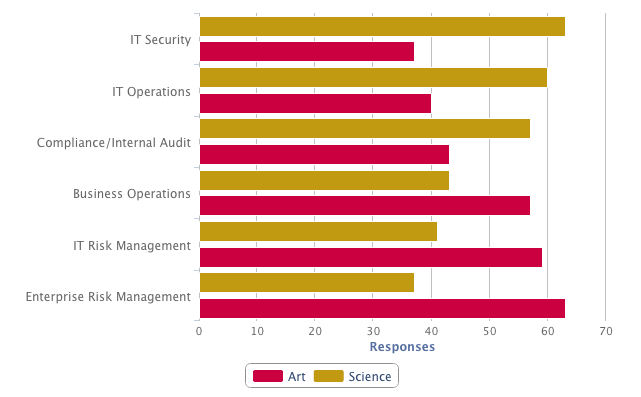
Is risk-based security management an art or science? That’s one key question posed to more than 1,200 IT professionals in a recent survey by Tripwire Inc. and Ponemon Research. The report, “The State of Risk Based Security 2013,” asked: “In your opinion, is information security risk management an ‘art’ or ‘science’?” For the purposes of the survey, “art” was defined as analysis and decision-making based on intuition, expertise and a holistic view of the organization. “Science” refers to risk analysis and decision-making based on objective, quantitative measures. They found:
- In the U.S., 49% of respondents said “art” and 51% said “science”
- In the UK, 58% of respondents said “science” and 42% said “art”
- 66% of enterprise risk managers and 62% of business operations respondents say risk based security management is “art”
- 62% of IT security and 56% of IT operations said “science”
“Business operations and risk managers tend to view risk management as more of an art because they don’t feel a precise answer is needed to be able to make a decision,” said Dwayne Melancon, chief technology officer for Tripwire. “People in these roles are looking for directional information to guide their decisions. On the other hand, IT operations and IT security departments tend to view security risk management as a math problem that has a very precise answer. People with these viewpoints are talking about the same thing, but they are using very different language, which can make it difficult to come to a mutually agreed point of view.”
The findings illustrate the diversity of opinion on the use of risk-based security management in the organization. These differences of opinion, those often times valued, can can potentially complicate communication and collaboration that is necessary within a business setting.
The following is an analysis of responses by job title: