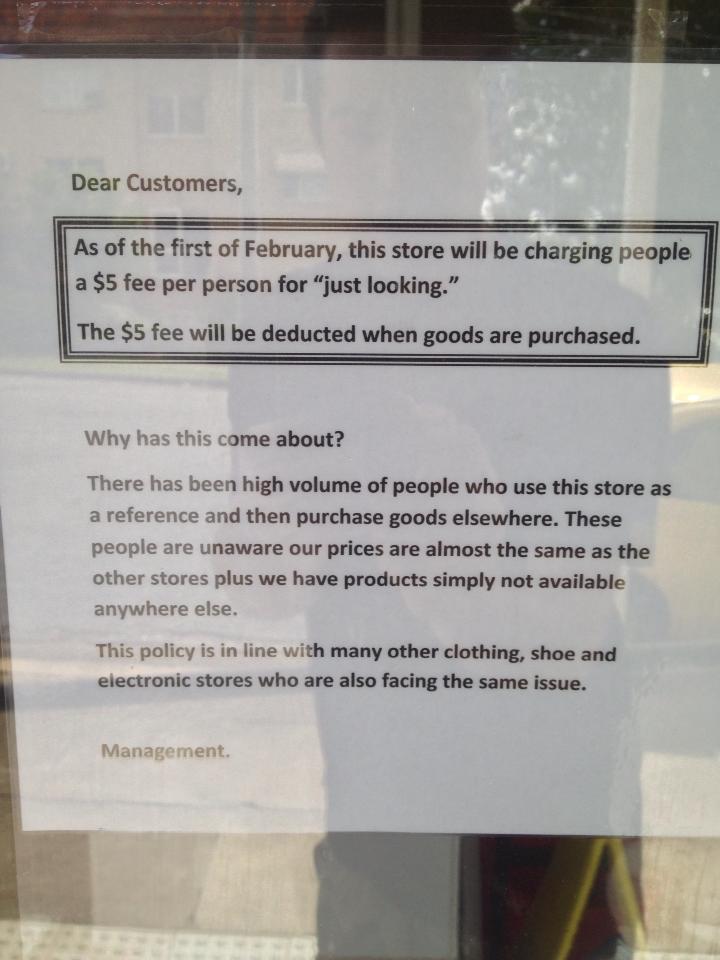
 As traditional brick-and-mortar retailers continue devise ways to combat “showrooming” (the practice where customers browse store shelves to check out items that they ultimately intend to buy online), it seems that one retailer has come up with a new plan — charge customers for “just looking.”
As traditional brick-and-mortar retailers continue devise ways to combat “showrooming” (the practice where customers browse store shelves to check out items that they ultimately intend to buy online), it seems that one retailer has come up with a new plan — charge customers for “just looking.”
According to the above photo posted this week on Reddit, a specialty food store in Brisbane, Australia has decided to charge customers a $5 fee for browsing, which they will refund from the purchase price of whatever they buy. Somehow they think that charging what amounts to an admission fee to enter their store will be good for business, but treating prospective customers like the enemy sounds like the worst marketing strategy ever.
It’s almost as if they’re encouraging people to go online.
It seems to me that if their prices were truly “almost the same as other stores” as they claim, they wouldn’t have this problem. And if their products are unavailable anywhere else, how is showrooming even an option?
Logical issues aside, showrooming is certainly a problem for retailers. But wouldn’t a price matching policy, like the one Target chose to put in place, be a more effective way to fight it? Or how about making your store a more inviting place to shop by welcoming your customers with a personal touch they can’t get online? As I understand it, usually the goal for retailers is to get more people into your store, but what do I know?
I guess policies like this are yet another reason why not every business can be a success.


