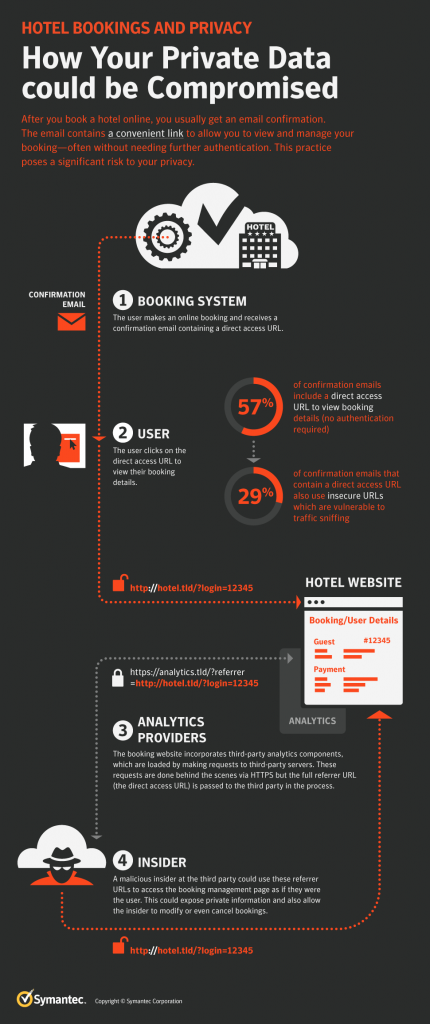
Regulatory change management (RCM) is one of the most important risk and compliance related domains in 2021, thanks to two key drivers. First, the shift from Republican deregulation to Democratic control and an expected uptick in regulatory requirements. Second, similar to the 2008 crash, the pandemic-induced economy and focus on Paycheck Protection Program (PPP) loans caused many banks to relax their regulatory exams and requirements, while regulators gave companies extra runway for transitioning processes and policies for remote/work-from-home models.
Sometimes regulatory changes are significant enough to change business strategy. In 2021, chief risk officers must be prepared to quickly adapt and react to a historically volatile risk management environment.
When thinking about an updated, strategic regulatory change management program, here are six considerations for chief risk officers:
1. Lax compliance during the pandemic in 2020 may have introduced hidden risk for activities that normally would have had deeper oversight.
Sometimes rule changes can also introduce new risks or eliminate a previous risk that needed to be managed, such as potential new default rates around extensions, forfeiture and other things. For example, historically low interest rates present a vexing risk for banks dealing with less profit but just as many loans to process.
What kind of new risk may be found within those loans?
2. When communicating change across the enterprise, establish responsibility to manage it.
Once you understand which regulations have changed, prioritize those that present the most risk, identify what department’s products and processes are impacted, and determine who is responsible for managing those policies. Having a secure central repository for communicating, storing and managing compliance documentation, versus relying on employees storing information on devices outside corporate servers, is ideal.
3. If conducting quarterly testing of compliance requirements, it may be challenging to identify key areas in advance that could slip, such as controls around IT/cybersecurity.
When the risk portfolio changes, the controls to manage those risks must be updated accordingly. Firms that may now be less dependent on management oversight and more dependent on confirmations that processes are being followed should put automated controls in place to verify those activities.
4. Companies should shift to best practice or common checklists that can be standardized and shared across the enterprise.
Assessment checklists are a great way to ensure that all requirements are being met for a wide variety of business processes. Once checklists have been updated, cloud-based software systems can track who has access and can also notify when changes happen.
5. Historically done manually in-house by visible teams, monitoring and testing for compliance purposes will be conducted remotely.
The visibility of those tests presents significant challenges, and it is critical to determine how errors and issues will progress and be communicated to the remote testing teams, management, and the organization at large.
6. Verifying and certifying online training for remote employees can be daunting.
Creating courses formalized for online training represents a major compliance and process change, particularly for companies in industries with limited work-from-home models, such as financial services. Training materials will need to be updated for new employees, while previously trained employees will need to be retrained.